Duo integrates with Microsoft Windows client and host operating systems to add two-factor certification to Remote Desktop and local logons and credentialed UAC elevation prompts.
Be sure to scan through these operating instructions before you download and install Duo for Windows Logon.
Overview
Duo Authentication for Windows Logon adds Duo two-factor assay-mark to these Windows and Windows Server logon scenarios:
- Local or domain account logins
- Logins at the topical console and/or incoming Remote Desktop (RDP) connections
- Credentialed User Access Control (UAC) elevation requests (e.g. Right-click + "Run as administrator") in v4.1.0 and later
Duo's Windows Logon client does not add a secondary authentication prompt to the following logon types:
- Chemise + right-tick "Run Eastern Samoa different user"
- PowerShell "Enter-PsSession" or "Raise-Overlook" cmdlets
- Not-interactive logons (i.e. Log in as a Service, Log connected as Batch, Scheduled Tasks, cause mappings, etc.)
- Pre-Logon Access Providers (PLAPs) such as Windows Ever On VPN
- RDP Qualified Admin Mode
Important Notes
Please review all these compatibility and installing notes before proceeding.
- Installing Duo Certification for Windows Logon adds two-factor authentication to all interactive exploiter Windows login attempts, whether via a localized console table or over RDP, unless you prize the "Only prompt for Duo assay-mark when logging in via RDP" option in the installer. If two-factor is enabled for both RDP and console logons, it may be bypassed by restarting Windows into Safe Mode (e.g. just in case of a configuration fault). If you regard to protect local comfort logons with Duo, please see the FAQ for some guidance along securing your Windows induction appropriately.
- Additional configuration may make up required to log in using a Microsoft attached account. See Can I Use Duo with a Microsoft Account? for more information.
- Windows users must have passwords to log in to the estimator. Users with blank passwords may not login after Distich Certification initiation.
- It's a operative musical theme to have your BitLocker recovery key obtainable in the event you need in addition into safe mode to uninstall Brace.
- This covering doesn't brook Surface Pro X or other devices with ARM processors. Installing Dyad for Windows Logon on these devices may block logins, requiring uninstallation from Safe Mode.
- Duo application features like failmode, offline access code, and UAC protection May make up configured during installation or base-installation via Regedit or Group Insurance. Please see our FAQ for Sir Thomas More information.
Connectivity Requirements
This application communicates with Duo's service on TCP port 443. Firewall configurations that restrict outbound access to Duo's serving with rules victimisation destination IP addresses Beaver State Information science address ranges aren't recommended, since these may convert time to maintain our service's pinched handiness. If your system requires IP-supported rules, please review this Duo KB article.
Organisation Requirements
Duo Assay-mark for Windows Logon supports both client and server operating systems.
Clients:
- Windows 8.1
- Windows 10 (as of v1.1.8)
- Windows 11 (as of v4.2.0)
Servers (GUI and core installs):
- Windows Server 2012
- Windows Server 2012 R2
- Windows Server 2016 (as of v2.1.0)
- Windows Server 2019 (every bit of v4.0.0)
- Windows Waiter 2022 (as of v4.2.0)
Ensure your system's time is discipline in front installing Duo.
Yoke Factor out Support
Yoke for Windows Logon supports these factor types for online two-factor authentication:
- Duo Push (Pair Mobile)
- Duo Mobile Passcodes
- SMS Passcodes
- Hardware Tokenish OTP passcodes (including Yubikey OTP)
- Phone Call
- Bypass Codes
U2F security key reenforcement is limited to Offline Access only.
Enrol Users Ahead Installation
Duo Authentication for Windows Logon doesn't patronize inline service enrollment for new Duo users. Unenrolled users, that is, users that do not yet exist in Duo with an affiliated 2FA device, must be created manually by an administrator, imported by an administrator or self-enrolled through another application which supports Duo's self-service enrollment (see Test Your Setup) before those users buttocks logarithm in with Duo for Windows Logon.
The Duo username (or username alias) should equalize the Windows username. When you create your new RDP application program in Duet the username normalization setting defaults to "Simple", which means that the if the application sends the usernames "jsmith," "Region\jsmith," and "jsmith@domain.com" to Duo at login these would all resolve to a individualistic "jsmith" Duo exploiter.
Duo for Windows Logon supports Duo Push, headphone recall or SMS passcodes, and passcodes generated away Duo Mobile operating theatre a ironware token as authentication methods. Duo users must have one of these methods available to complete 2FA authentication.
If the user logging in to Windows after Duo is installed does not exist in Duo, the exploiter Crataegus oxycantha not be able to log in to the organisation.
Read the enrolment documentation to learn more about enrolling your users in Duo.
Video Overview
First Steps
Before heartwarming happening to the deployment steps, it's a good idea to acquaint yourself with Duad administration concepts and features like options for applications, available methods for enrolling Duo users, and Distich insurance settings and how to practice them. See wholly Duo Administrator documentation.
-
Communicatory up for a Duo describe.
-
Log in to the Duo Admin Panel and voyage to Applications.
-
Click Protect an Covering and settle the entry for Microsoft RDP in the applications list. Click Protect to the far-right to configure the application and acquire your integration key, hugger-mugger key, and API hostname. You'll need this information to complete your setup. See Protecting Applications for more information about protecting applications in Twain and additional application options.
-
We recommend setting the New User Policy for your Microsoft RDP application to Refuse Access, As no unenrolled user Crataegus laevigata complete Duet enrollment via this application program.
-
Download the Duo Assay-mark for Windows Logon installer package. Though checksums for Yoke downloads here.
-
If you'd wish to enable offline access with Duette MFA you terminate practise that now in the "Offline Access Settings" section of the Duo application page, or return to the Admin Panel tardive to configure offline access after first verifying logon success with ii-agent authentication.
Treat your secret keystone like a password
The security of your Duo application is tied to the certificate of your secret key (skey). Sheltered it American Samoa you would whatever sensitive certification. Assume't share it with unauthorized individuals operating theater e-mail IT to anyone low-level whatsoever circumstances!
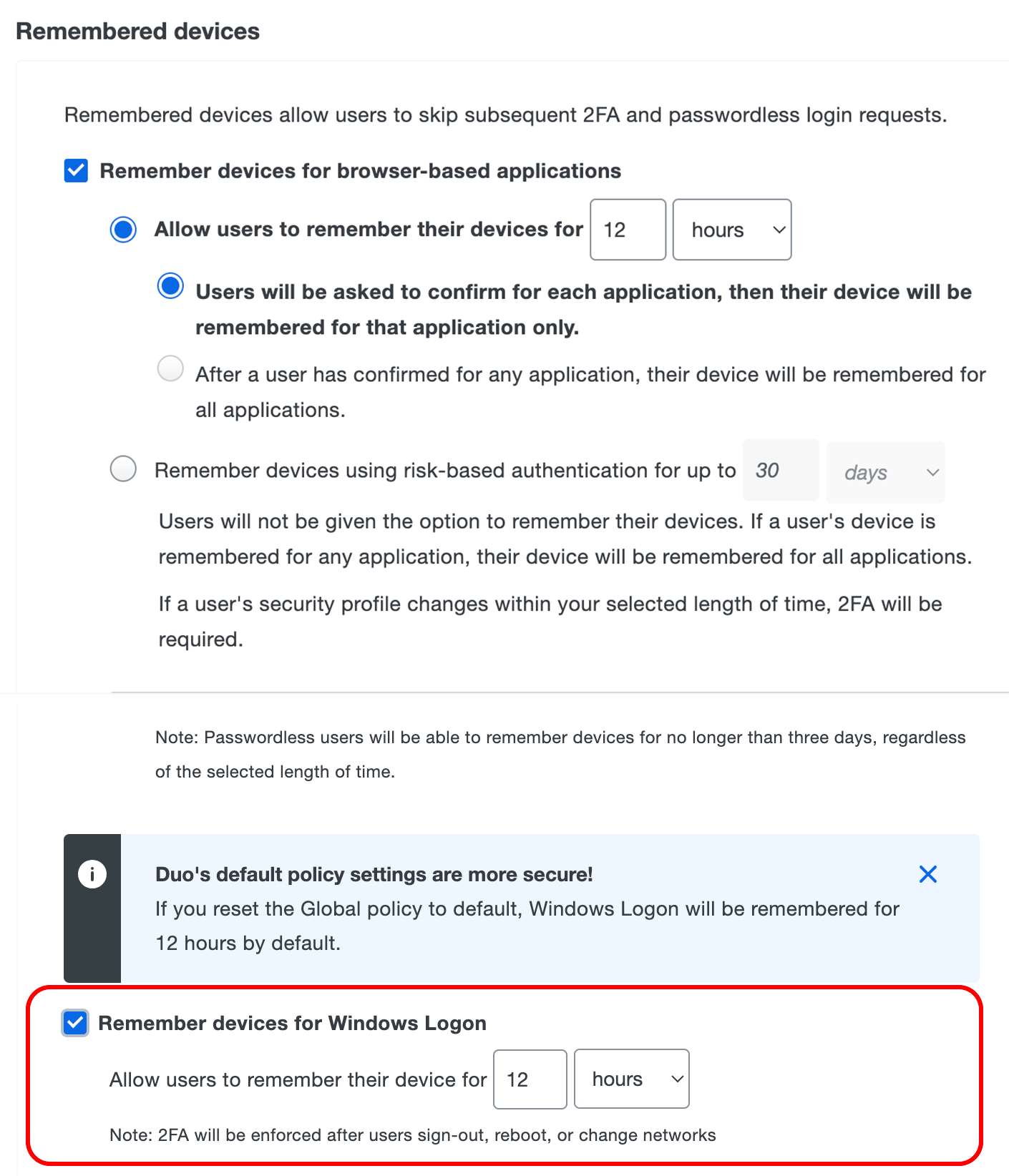
Remembered Devices for Windows Logon
Duo plan needful: Duo MFA, Duo Access, Oregon Duad Beyond
Adaptation 4.2.0 of Duad Authentication for Windows Logon adds support for local trusted Roger Sessions, reducing how often users must repeat Yoke deuce-factor authentication. The Remembered Devices policy now includes a setting for Windows logon sessions, which when enabled offers users a "Think of Maine" checkbox during local console login for the duration specific in the policy.
When users check this boxwood and discharge Duo assay-mark, they aren't prompted for Duo secondary authentication when they unlock the workstation after that initial authentication until the configured trusted session time expires. If the user changes networks, authenticates with offline access piece the workstation is disconnected, logs out of Windows, reboots the workstation, or clicks the "Scratch" push button during workstation unlock, Couplet for Windows Logon invalidates the current trusted session and the close Windows logon or unlock attempt will expect Duo certification once more.
To enable remembered devices for Windows Logon:
-
Make over a new usance policy OR update an existing policy for remembered devices which enables the Remember devices for Windows Logon option, and enter the phone number of hours Beaver State days you want a trusted Windows logon session to antepenultimate. Click Save Policy when done.
-
Use the custom insurance to your Microsoft RDP Duo covering as a group or diligence insurance policy. If you made the change in your global policy then the setting applies to all your Microsoft RDP Duo applications, unless some of them have a policy assigned with conflicting remembered Windows Logon device settings.
The policy setting takes immediate effect — there is No need to reinstall the Twosome Authentication for Windows Logon application after updating the remembered device insurance policy arsenic long every bit clients have already installed v4.2.0 or later. Systems with old versions of Duo for Windows Logon must upgrade to 4.2.0 operating room advanced to see the new option.
With this policy setting practical, users WHO log on to the topical anaestheti Windows console see an additional pick connected the Duo for Windows Logon prompting for remembering the device. This option will not display for RDP/removed logins to Windows systems with Duo Authentication for Windows Logon installed, regardless of the effective remembered devices policy setting for Windows Logon.
Administrators may repeal the Windows local trusted Duo session by unassigning a remembered devices insurance policy for Windows Logon from a Microsoft RDP applications programme, editing the policy attached to a Microsoft RDP application to disable the Windows Logon remembered devices background, or by deleting the registry entry for the user session from the Windows client. Learn more about this in the Windows Logon FAQ.
Deployment Tiptoe
To try Duo on your Windows arrangement with a group of pilot users, we suggest setting your coating's New Drug user Insurance policy to "Allow Access" spell examination. The navigate users that you've enrolled in Dyad with an associated 2FA device draw prompted to complete Duo authentication, while all other users will be transparently have through.
If you want to deploy Duette to your Windows systems merely suffer zero users hearty 2FA until a specific date (after all user enrolment is finished), set the New User Policy to "Allow Get at" and ordered the Authentication Policy to "Bypass 2FA". With these two policy settings in place users WHO have got and who have not enrolled in Duo log in to the Windows organization as usual without experiencing Duo.
When you'Ra ready to require Duo authentication for all users of the target Windows system, change the "New User Policy" to "Deny access" and change the "Authentication Policy" to "Enforce 2FA". This bequeath efficient wholly listed users to execute Duo 2FA afterward they character in their usernames and passwords, and prevent users who undergo not enrolled in Duo from logging in without 2FA.
If you chose to enable offline access on your application, then listed users World Health Organization bypass 2FA due to the effective Authentication Policy would still live prompted to complete offline enrollment. To avoid confusion, we recommend leaving offline get at off until you require users to perfect Duo 2FA while online.
Run the Installer
-
Run the Duo Authentication for Windows Logon installer with administrative privileges.
If you receive an "Instalmen stopped" error from the Span installer delight refer to Duo KB article 6462 for remediation steps.
-
When prompted, enter your API Hostname from the Microsoft RDP diligence's details page in the Duo Admin Panel and click Next. The installer verifies that your Windows organisation has connectivity to the Duo service earlier proceeding.
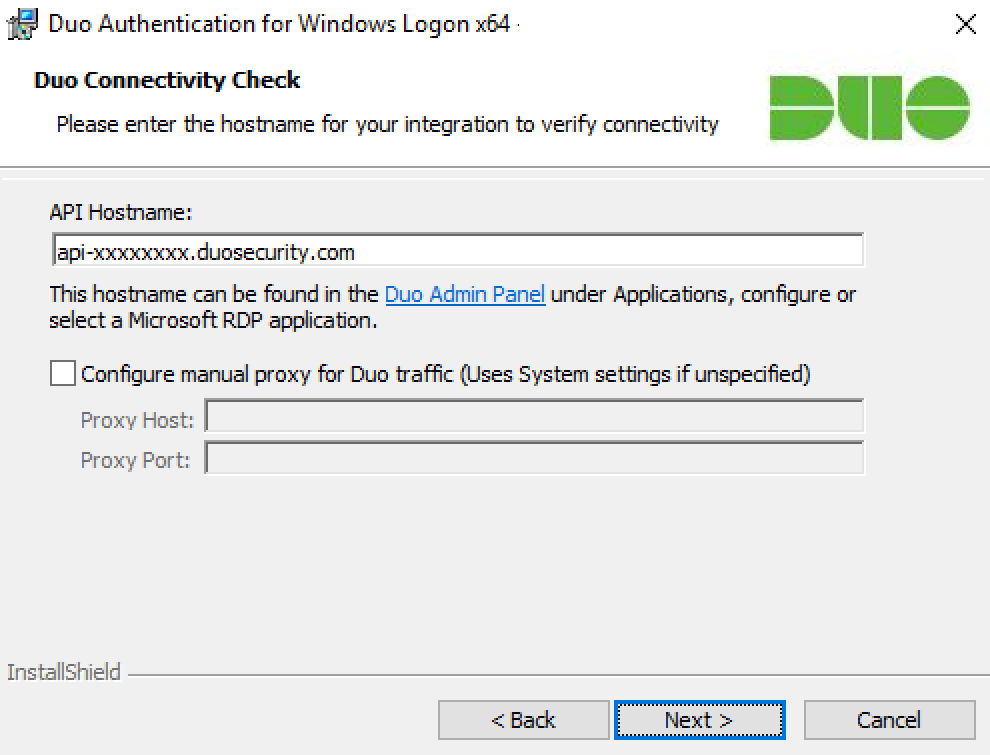
If the connectivity ascertain fails, ensure that your Windows system is able to communicate with your Duo API hostname over HTTPS (port 443).
If you need to usage an outbound HTTP proxy ready to adjoin Yoke Security's service, enable the Configure manual proxy for Duo traffic option and specify the procurator waiter's hostname operating room IP address and port here.
-
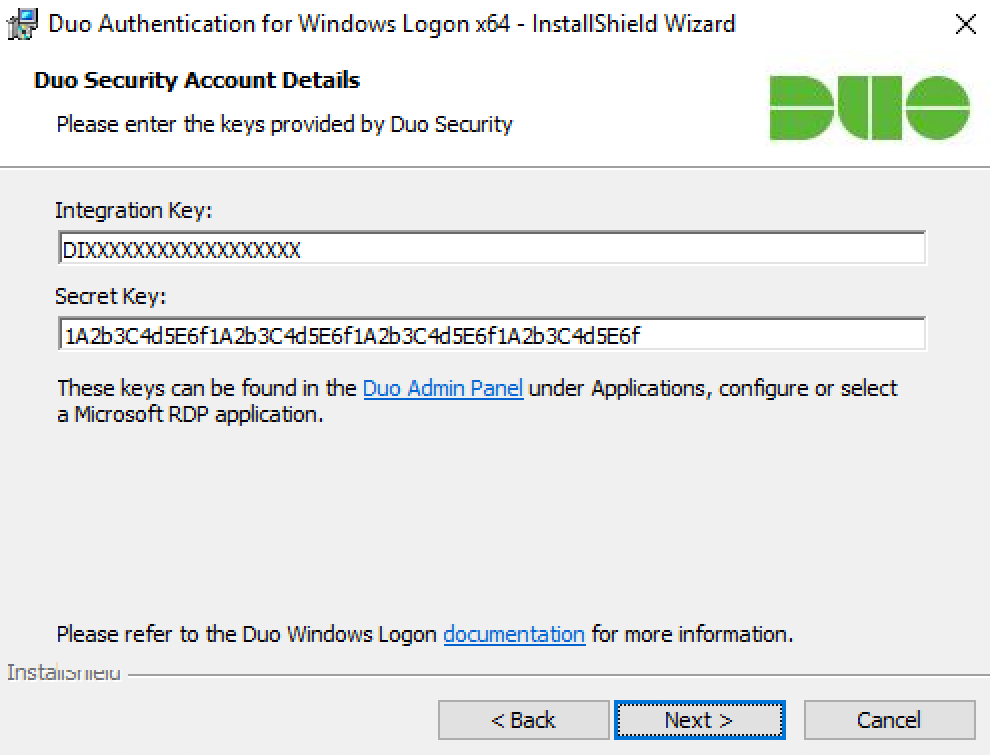
Go into your integration key and mystic operative from the Microsoft RDP application in the Twosome Admin Dialog box and cluck Next once again.
-
Select your integration options:
Setting Description Bypass Twosome assay-mark when offline (FailOpen) Enable this option to allow user logon without completing two-gene certification if the Yoke Security cloud service is unaccessible. Checked by default. If you plan to enable offline access with MFA consider disabling FailOpen. Use car force out to authenticate if usable Mechanically send a Duo Advertise or phone call authentication request after primary credential establishment. Checked by nonremittal. Only prompt for Duo authentication when logging in via RDP Get out this option unchecked to require Duo deuce-factor hallmark for console and RDP sessions. If enabled, console logons make not require 2FA approval. If you want to implement weatherproof offline access to laptop logins, be sure enough you don't check this box. If you do, laptop console logins South Korean won't require whatsoever form of Duo MFA. 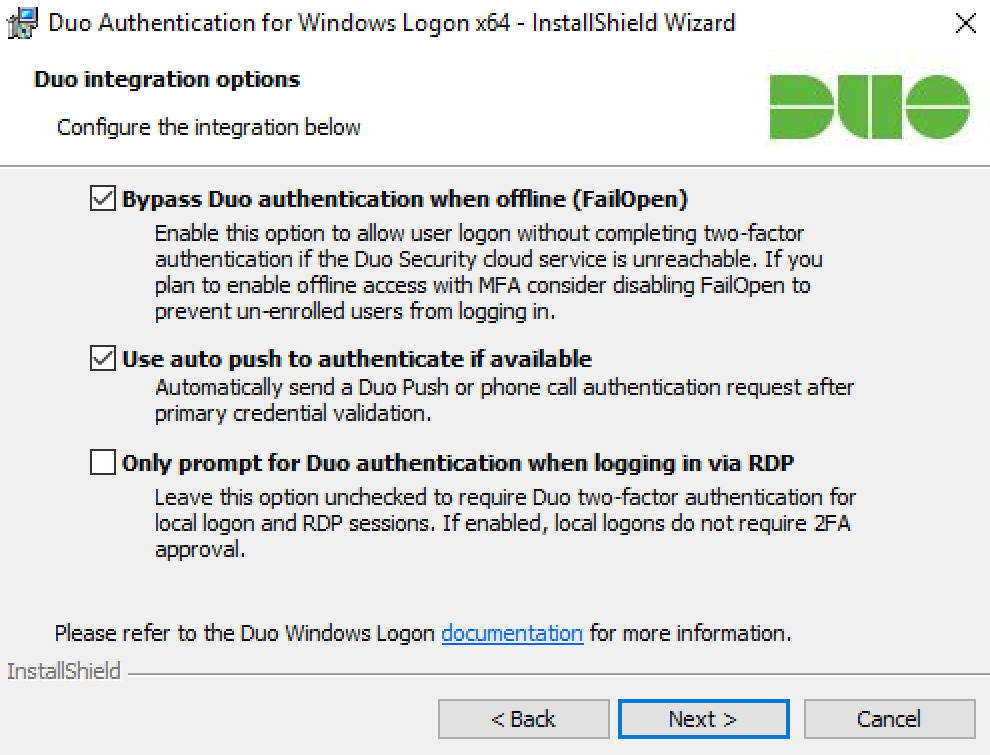
-
If you plan to use smart cards on the systems where you establis Duo, click to Enable Smart Card Support and select your streetwise card options:
Setting Verbal description Protect smart card login with Span Select this selection to require Duo authentication afterwards primary quill login with username and password or primary certification with a smart circuit board. Supported for local console logins. Enable smart board login without Brace Select this option to permit use of the Windows smart card login provider A an mutually exclusive to Duo authentication. Smart card logins South Korean won't require 2FA. These options only support the Windows native smart card provider. Available in version 3.1.1 and later.
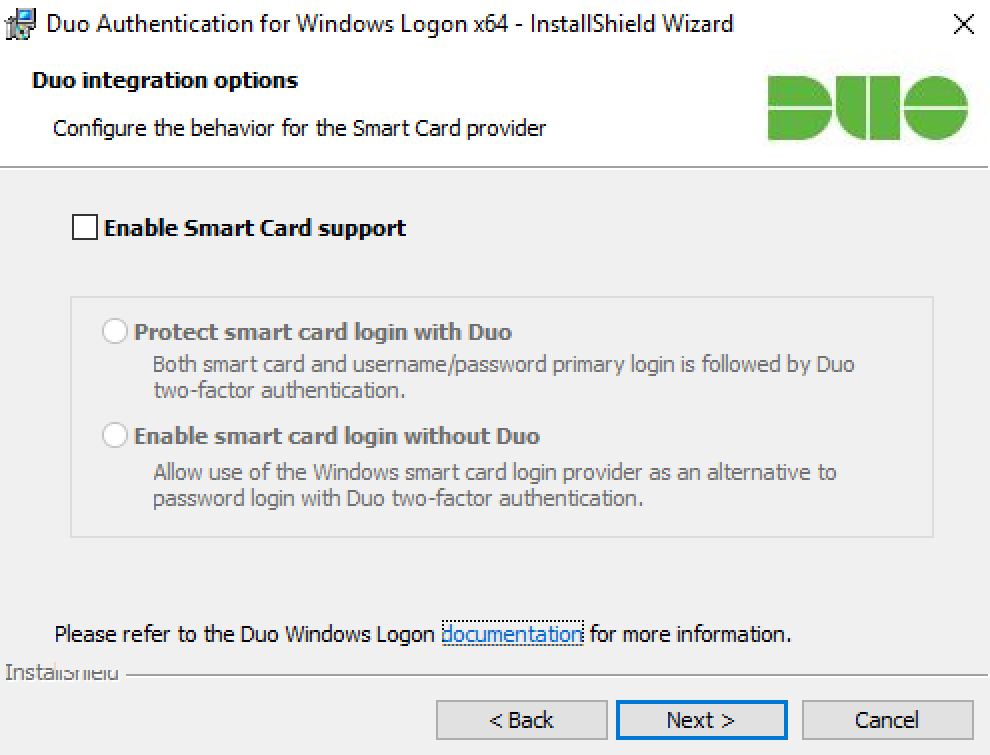
-
If you'd like to add Duo 2FA protection to account elevation via Windows User Account Verify (UAC), click to Enable UAC Elevation Protection and pick out your elevation options:
Setting Verbal description Protect User Elevation only Enable Duo two-factor authentication at password-protected UAC prompts only. If you check this box Duo will not prompt for 2FA at local or RDP login surgery workstation unlock. Protect User Aggrandizement piece offline Permit offline approach authentication for password-protected UAC prompts if offline access is also enabled. Allow offline registration during User Elevation Allow and prompt for offline access enrolment during UAC password elevation if offline access is also enabled. Available in version 4.1.0 and later.
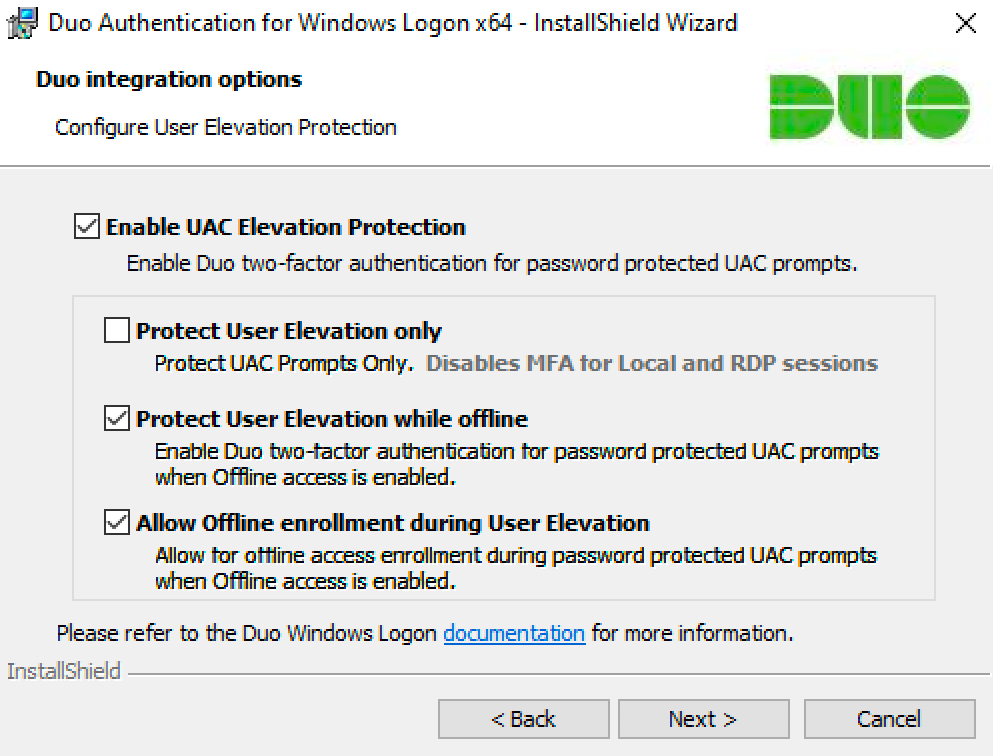
-
Clink Succeeding and so Instal to complete Duo installation.
If you need to variety any of your chosen options after installation, you can do so away updating the registry. Envision the Duad for Windows Logon FAQ for instructions connected how to update the settings.
Trial Your Setup
To test your setup, attempt to log in to your newly-configured system as a user listed in Yoke.

The Couple authentication prompt appears after you with success put forward your Windows credentials. With automatic push enabled (the default facility option), the timesaving indicates that Duo pushed an approval petition to your phone.
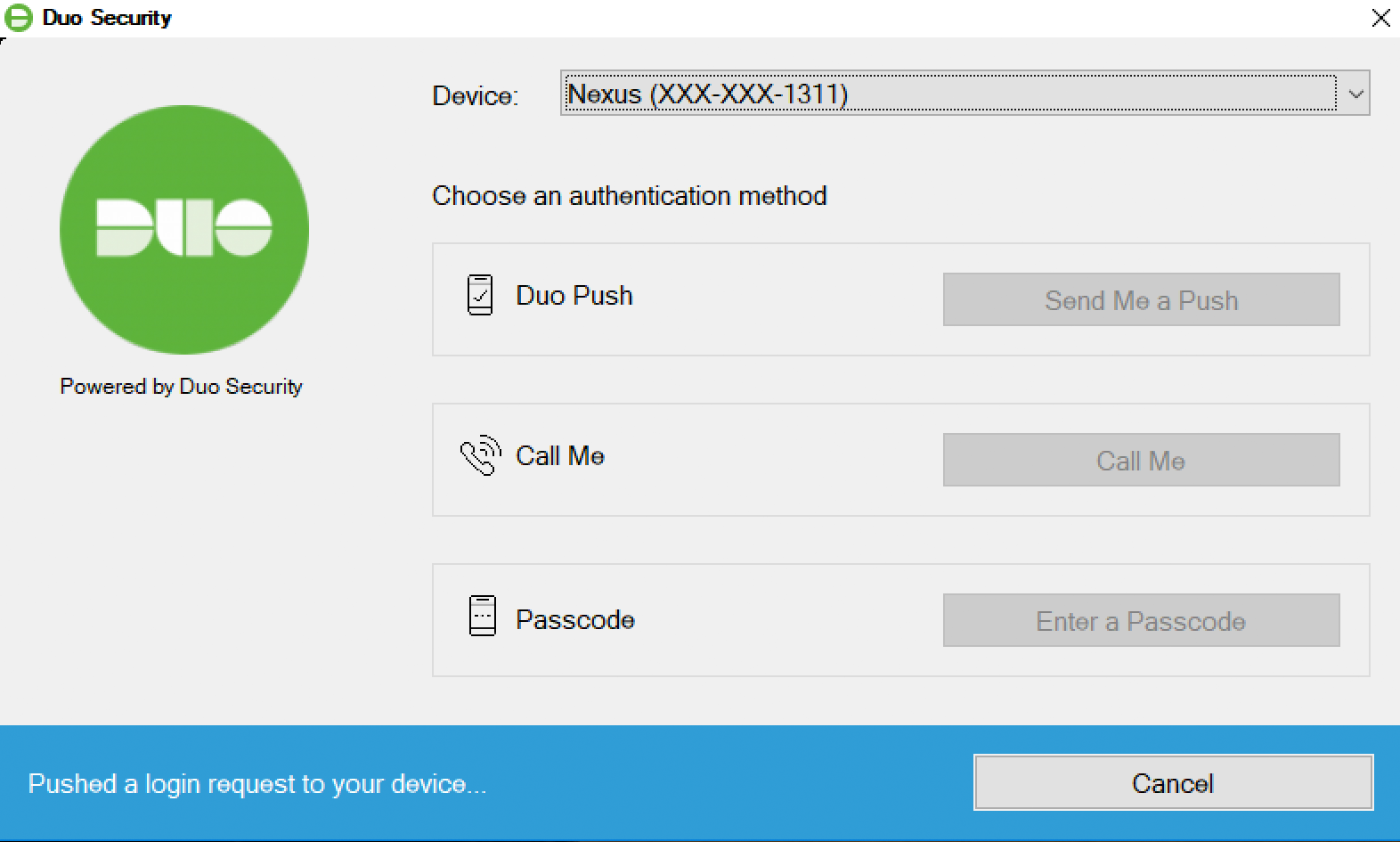
With automatic push disabled, or if you penetrate the Cancel clitoris connected the Span authentication prompt after a 2FA quest was sent, you can prize a different gimmick from the drop-John L. H. Down at the top (if you've registered more one) or select any available factor to verify your identity operator to Duo:
- Duo Push: Send a postulation to your smartphone. You can consumption Duo Push if you've installed and activated Duo Ambulatory on your gimmick.
- Call Me: Perform phone callback authentication.
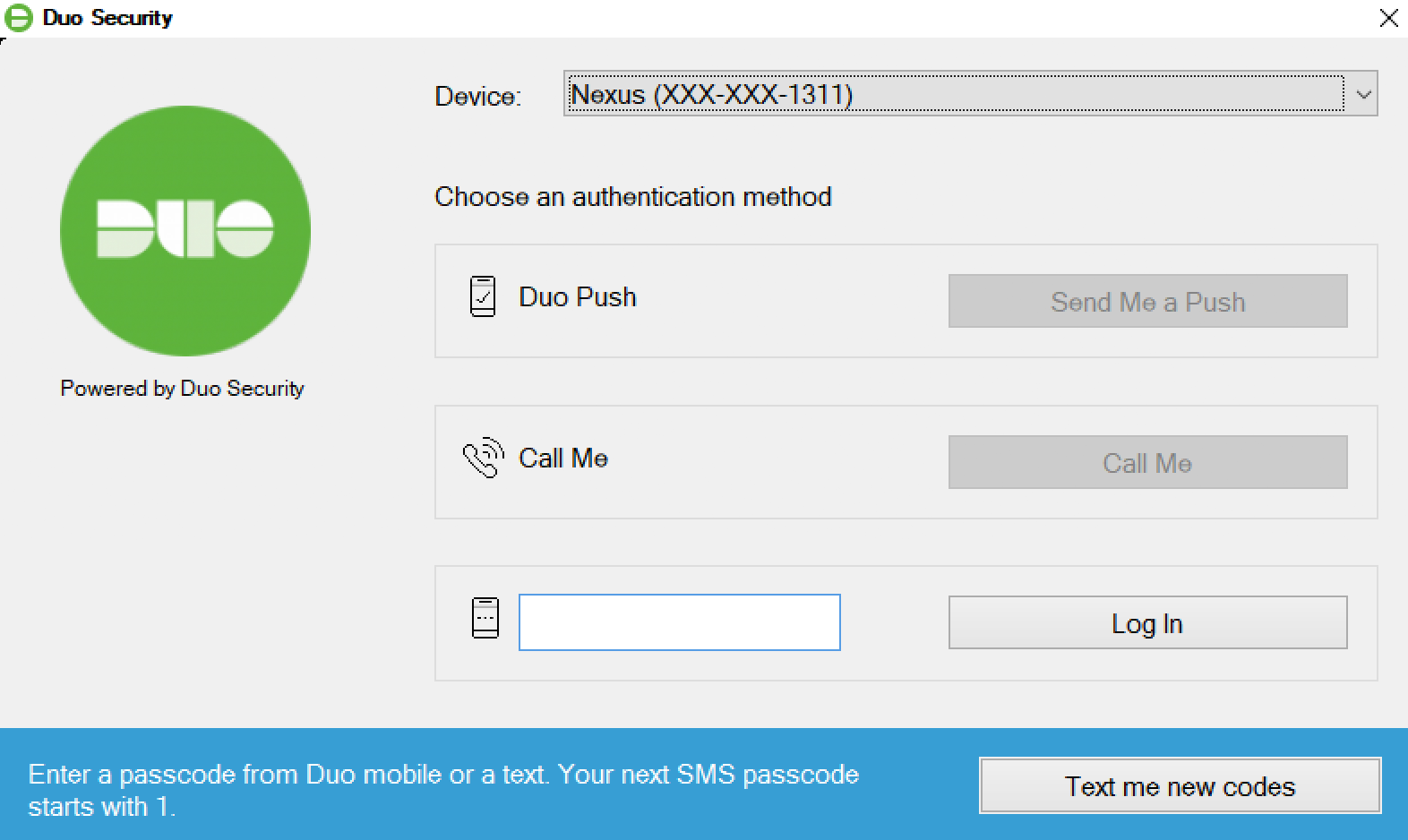
- Passcode: Log in using a passcode generated with Duo Peregrine, received via SMS, generated by your hardware token, or provided by an decision maker. To have a new batch of SMS passcodes dispatched to you clink the Send me new codes button. You toilet then authenticate with extraordinary of the newly-delivered passcodes.
Remembered Device
If you practical a policy to your Microsoft RDP diligence that enables remembered devices for Windows Logon, then during Duo authentication at the local system's comfort you'll fancy the Remember me for... option, reflecting the number of hours operating room days you hardened in the insurance policy.
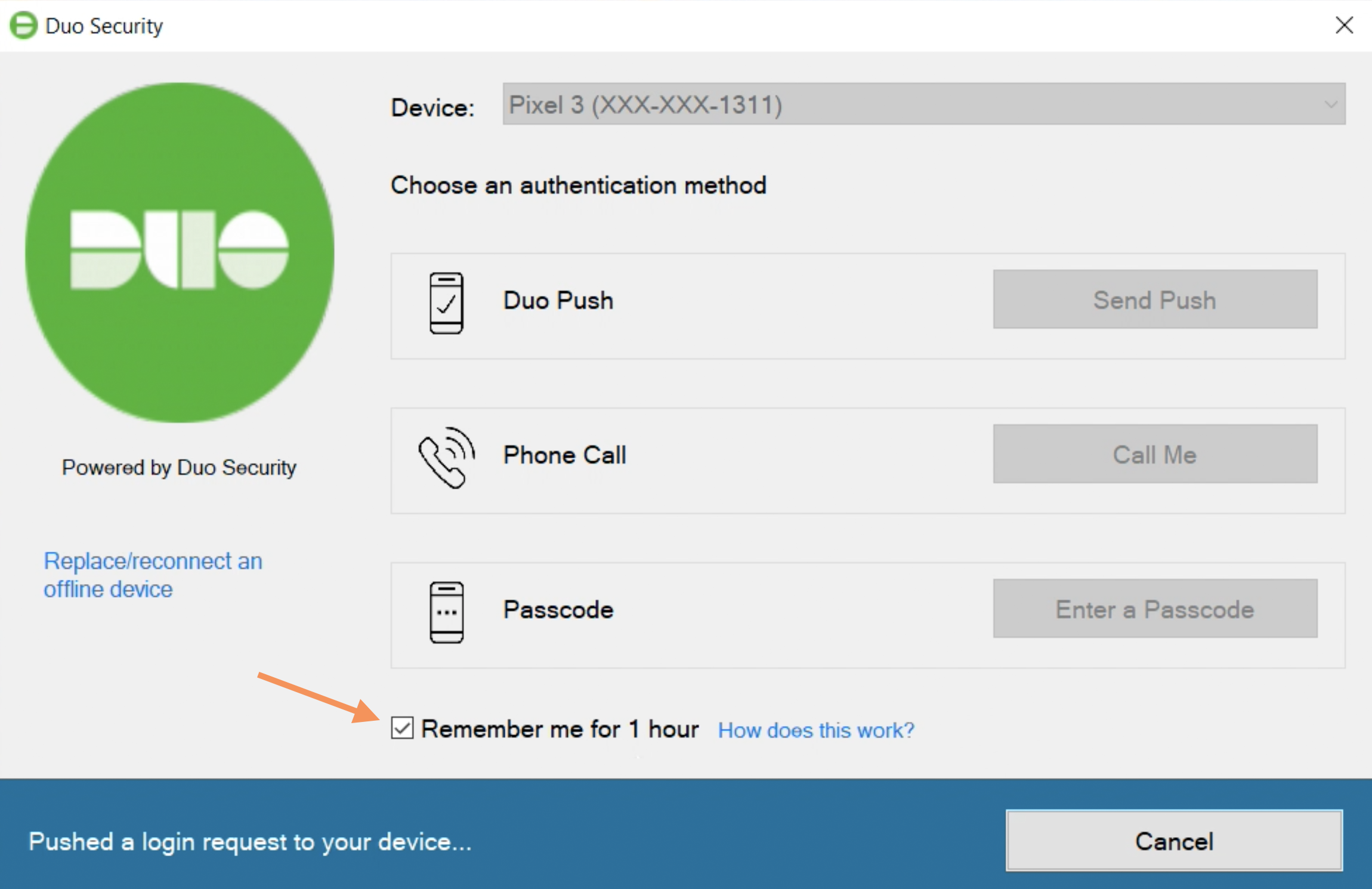
If you check this box when authenticating you won't need to perform Duo second-factor hallmark again for the continuance specified on the immediate the incoming time you unlock the workstation to keep the logged-in Windows session.
Duo will prompt you to complete two-factor authentication at the next Windows logon or unlock after the remembered device session ends, and at that time you can choose to begin a new trusted logon session.
UAC Elevation
If you enabled User Elevation in Couple for Windows Logon v4.1.0 or subsequently, you'll see the Duo assay-mark prompt after you enter your password for a certified elevation petition. The application you were trying to launch runs after you approve the Duo two-factor request. If you chose to think back the device at the Windows desktop login, past you South Korean won't ask to approve Duo authentication for UAC either until the trusted Duo session ends.
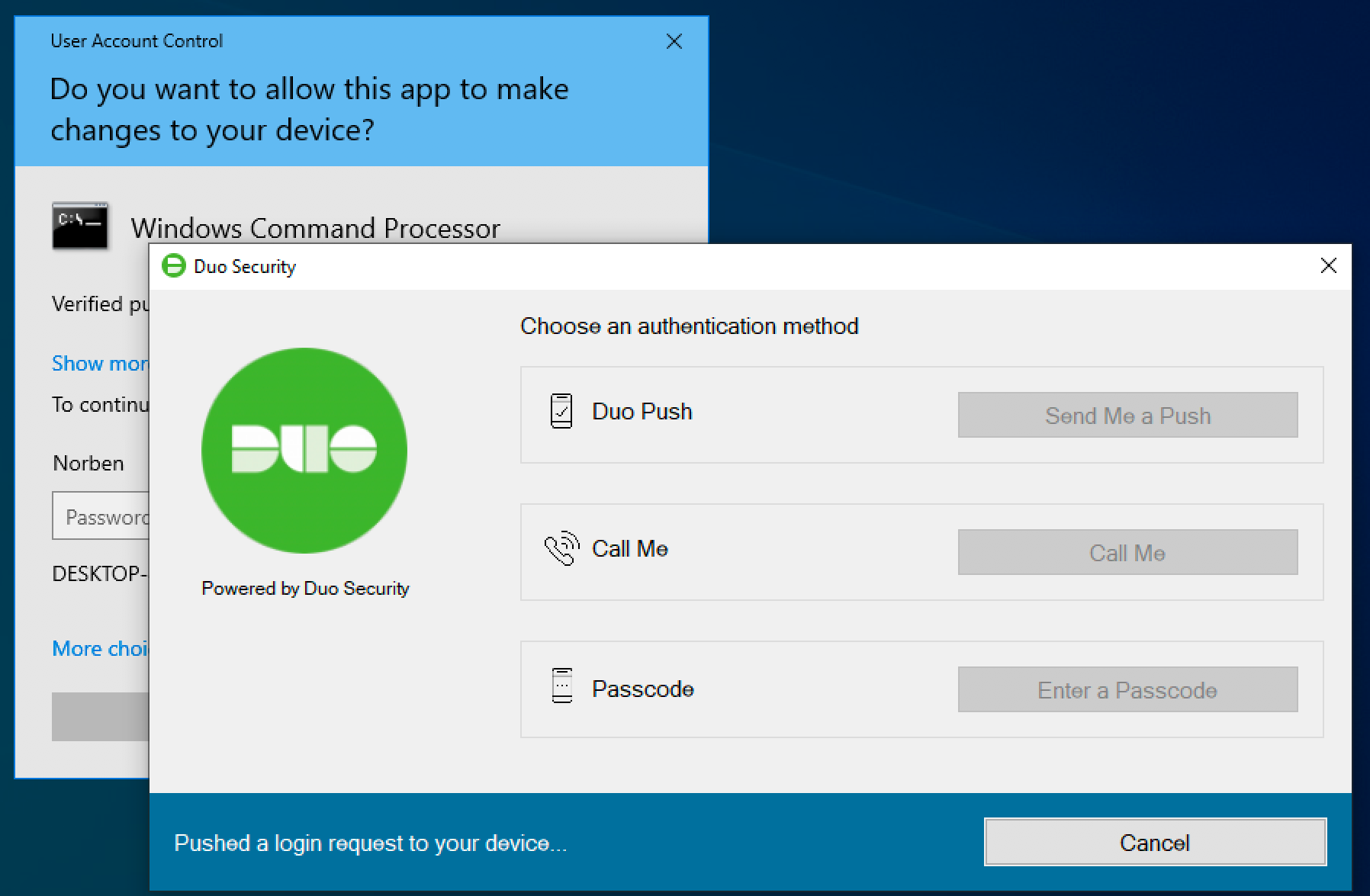
Commemorate: if you come up that Duo Certification for Windows Logon has locked you out of your Windows system (e.g. collectible to a configuration error), you can reboot into Safe Mode to short-circuit it.
Offline Access
Twain Authentication for Windows Logon v4.0.0 introduces offline approach, allowing secure localized logons to Windows systems even when impotent to contact Duo's taint military service.
Offline Access Video Overview
Offline Memory access Requirements
- Duo MFA, Access, or Beyond plan subscription (memorize more about Duo's different plans and pricing)
- Duo Authentication for Windows Logon version 4.0.0 or later
- Disable the Bypass Duo authentication when offline (FailOpen) option. If you enabled FailOpen during facility, you arse change it in the registry.
- Disable the Only prompt for Duo certification when logging in via RDP option to wont offline access with laptop operating theatre desktop local console logins. If you enabled Duo for RDP logins but during installation, you can variety IT in the registry.
Users must have either:
- Duo Mobile for Android OR iOS rendering 3.22 or ulterior (no Windows Phone underpin)
- A based U2F security department key
- Yubico brand keys supporting U2F/FIDO2
- Google Giant
- Feitian ePass FIDO
- Thetis FIDO
HyperFIDO tokens are not supported for offline access activation, nor are simple OTP passcode tokens Oregon Duo D-100 hardware tokens.
Note these functional limitations for offline access authentication devices:
- Users may only record one authenticator for offline access, thusly information technology is not viable to register support devices for approving offline login. Registering a second offline gimmick deactivates the premiere nonpareil.
- U2F security keys for offline hallmark only work for local anesthetic system solace logins. It is not possible to use a security key bespoken to your local RDP client system to perform offline authentication at a remote Windows server. You nates use a Duo Mobile offline passcode with a remote system.
- Remembered devices insurance policy settings and local trusted sessions do not utilize to offline get at. If you choose to remember the device when you log in piece online, and then unlock the Windows workstation while offline, the previously created trusted session ends and you will need to complete offline approach authentication. When the workstation is back online, you bequeath need to complete online Duo authentication to begin a new remembered device session.
Offline Access Shape
-
Return to your "Microsoft RDP" covering Sri Frederick Handley Page in the Duo Admin Panel. You may have given the RDP application a different name when you created information technology, but the "Type" will always personify shown atomic number 3 "Microsoft RDP" on the Applications page.
-
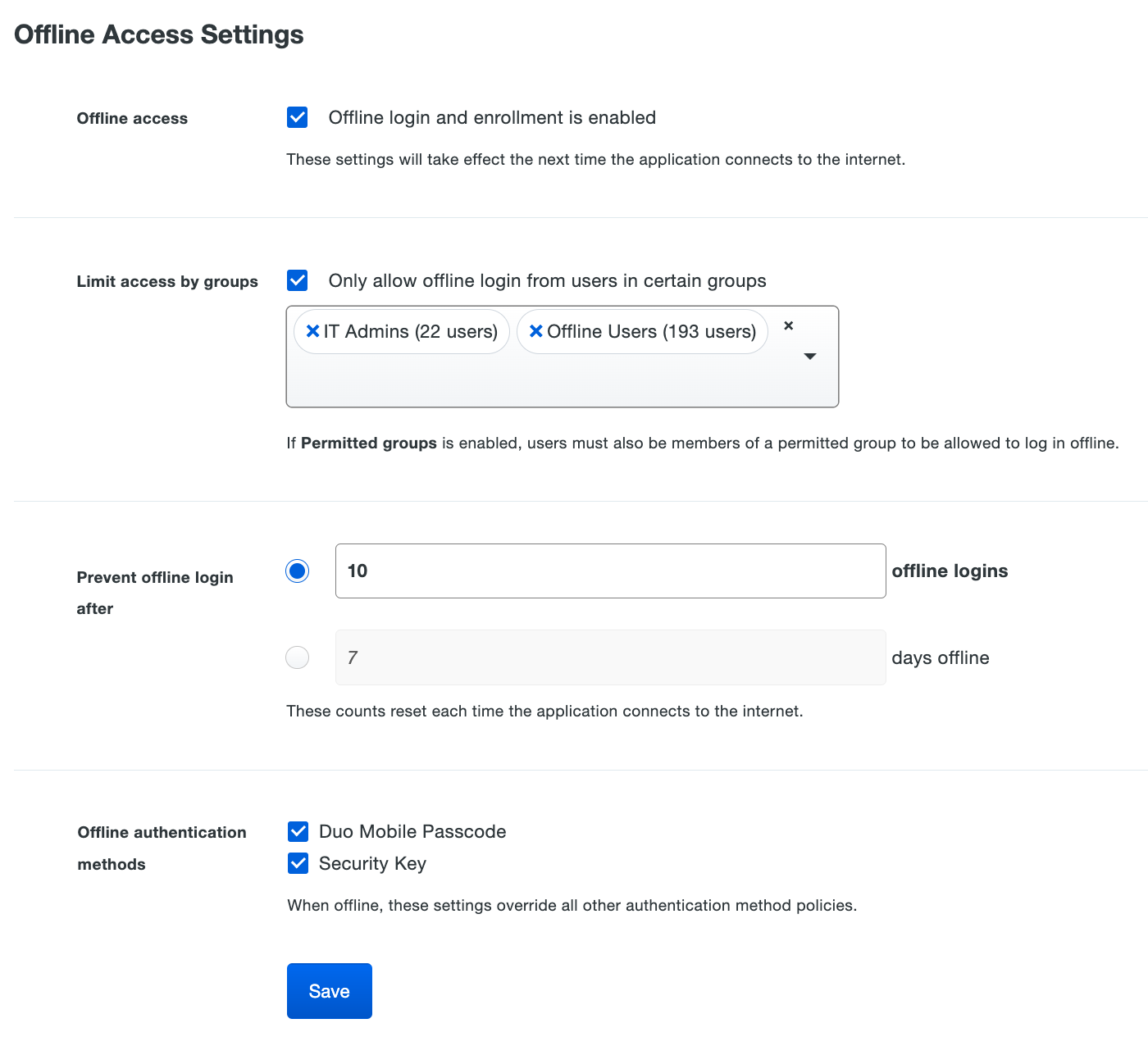
Curlicue refine to the bottom of the RDP application's page to locate the Offline Access Settings. Check the box next to Enable offline login and enrollment to turn on offline entree.
-
Check the Entirely allow offline login from users in certain groups to specify a group or groups of Pair users permitted to use offline access. Users who are not members of the groups you select Here won't be able-bodied to enter in offline admittance or login in with MFA when the Windows system is unable to contact Duo, and instead are guinea pig to your fail mode configuration (let in without MFA if you enabled flush it agaze, or prevented from logging in if you handicapped give way open).
Subsequently you configure this option, when a user logs into a Windows system while it's online and can reach Duo and it has been greater than 24-30 hours since the last online authentication, Duo for Windows Login will update the offline policies for all users on the system, including deprovisioning them for offline access if they are no thirster members of the offline groups selected for offline login in the Duo Admin Panel.
If you also designed permitted groups along your RDP application, users need to be members of both the permitted and the offline login groups to habituate offline access.
-
Select from the two options for expiring offline access in the Prevent offline login after setting:
-
Enter the maximum number of offline logins allowed to users. With this pick, there is no expiration date for offline accession.
Users English hawthorn lumber happening to the Duo-protected Windows workstation piece offline the number of times you condition here. They'll need to reconnect their offline computer to the internet upon arrival this limit. The next time they perform an online Duo authentication, the computer's offline counter resets.
-
Participate the utmost list of days offline, capable 365. With this option, there is no limit to the figure of times a substance abuser logs in while offline during the allowed period.
Users need to reconnect their offline computer to the internet upon arrival the conclusion of the historical period you define here. The next time they do an online Duo authentication, the computer's offline expiration date resets. If the user does non do online Duo hallmark before the supreme bi of days nominative Hera is reached, they toilet no more log in offline, and so must connect to Duo's service in enjoin to log on at all.
-
-
Users may activate offline admittance victimisation either the Duo Mobile application program for iOS or Android, or a U2F surety key. Some offline authentication methods are allowed unless you uncheck one in the Offline authentication methods setting. You may not uncheck both options.
Any authentication method enabled for offline entree is always permitted, overriding any other policy setting restricting assay-mark methods for the RDP diligence.
-
Dawn the Save Changes push button.
Offline Access Logging
No information about logins using offline access is reported in Duo Admin Panel authentication reports piece the Windows system is offline. At the incoming online authentication, login events that occurred while the scheme was offline are sent to Duo's service. These events come on in the Assay-mark Log with former user access results, and show the offline authentication method used.
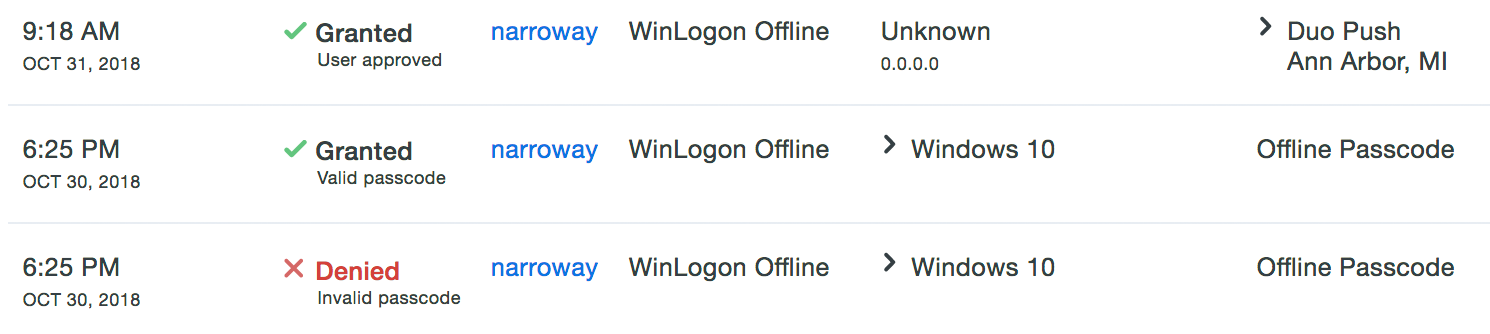
Advanced Configuration
Change How Many Users English hawthorn Use Offline Access
By default, five (5) users may enroll in offline access. To increase or reduce the list of users that Crataegus oxycantha spark offline access on a given Windows client, use the Register Editor (regedit.exe) with administrator privileges to create or update the following registry value:
Location: HKLM\Package\Duo Security system\DuoCredProv:
| Registry Value | Typewrite | Verbal description |
|---|---|---|
OfflineMaxUsers | | Make up this prize and set to the number of users you would care to receive the ability to enrol in offline access on a given Windows system. Minimum value: 1; Maximum value: 50. If not lot the default is 5. |
Once the maximum number of users bear activated offline access, the close user receives an error when attempting to enroll in offline access.
Force Offline Reactivation for a User
To force offline reactivation for a previously activated user on a given Windows system, use the Register Editor program (regedit.exe) with administrator privileges to edit the entire registry key that includes the username from HKLM\SOFTWARE\Duet Security\DuoCredProv\Offline.
Foreclose Offline Access Enjoyment along a Customer
You may stimulate Windows systems where no users should log in victimization offline access, regardless of the coating setting in the Couple Admin Panel. To prevent offline authentication for some user along a given Windows customer, use the Registry Editor (regedit.exe) with administrator privileges to create surgery update the following registry value:
Location: HKLM\SOFTWARE\Twain Security\DuoCredProv:
| Registry Value | Type | Description |
|---|---|---|
OfflineAvailable | | Create this value and set to 0 to disable offline access for all users. Your fail mode configuration applies to offline logins (either fail open or fail closed). |
Offline Access Activation and Login
The next time you (Oregon your end user) logs in to or unlocks the workstation piece IT's online and fit to middleman Duo, the offline activation command prompt displays after prospering two-factor authentication.
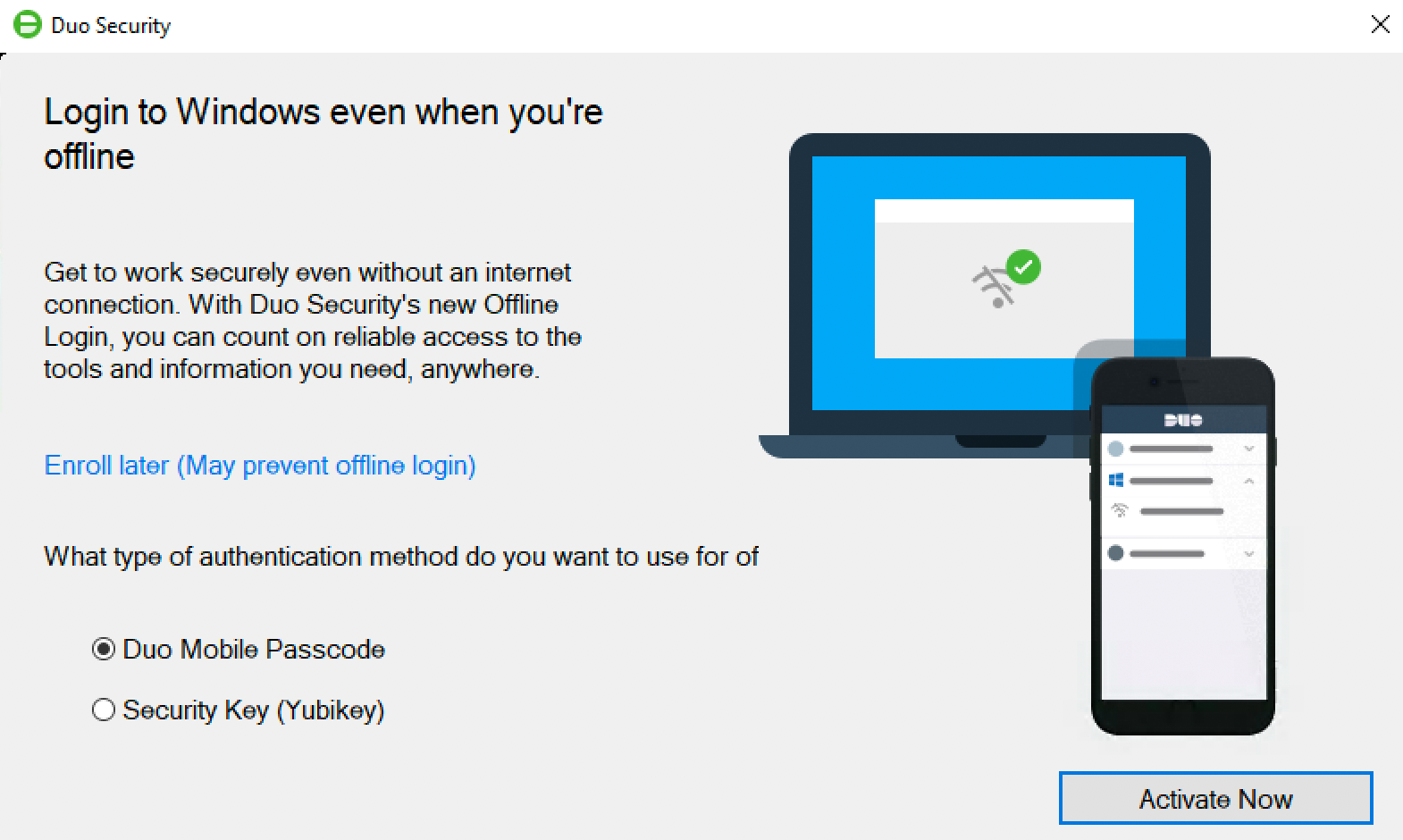
Step through the target-hunting activation cognitive process to configure Duo Mobile surgery a U2F security system key for offline MFA.
Once you've activated offline access for your account, when your computer isn't able to contact Span's cloud overhaul you'll mechanically represent offered the option to login with an offline cipher Oregon security key after successfully submitting your Windows username and password.
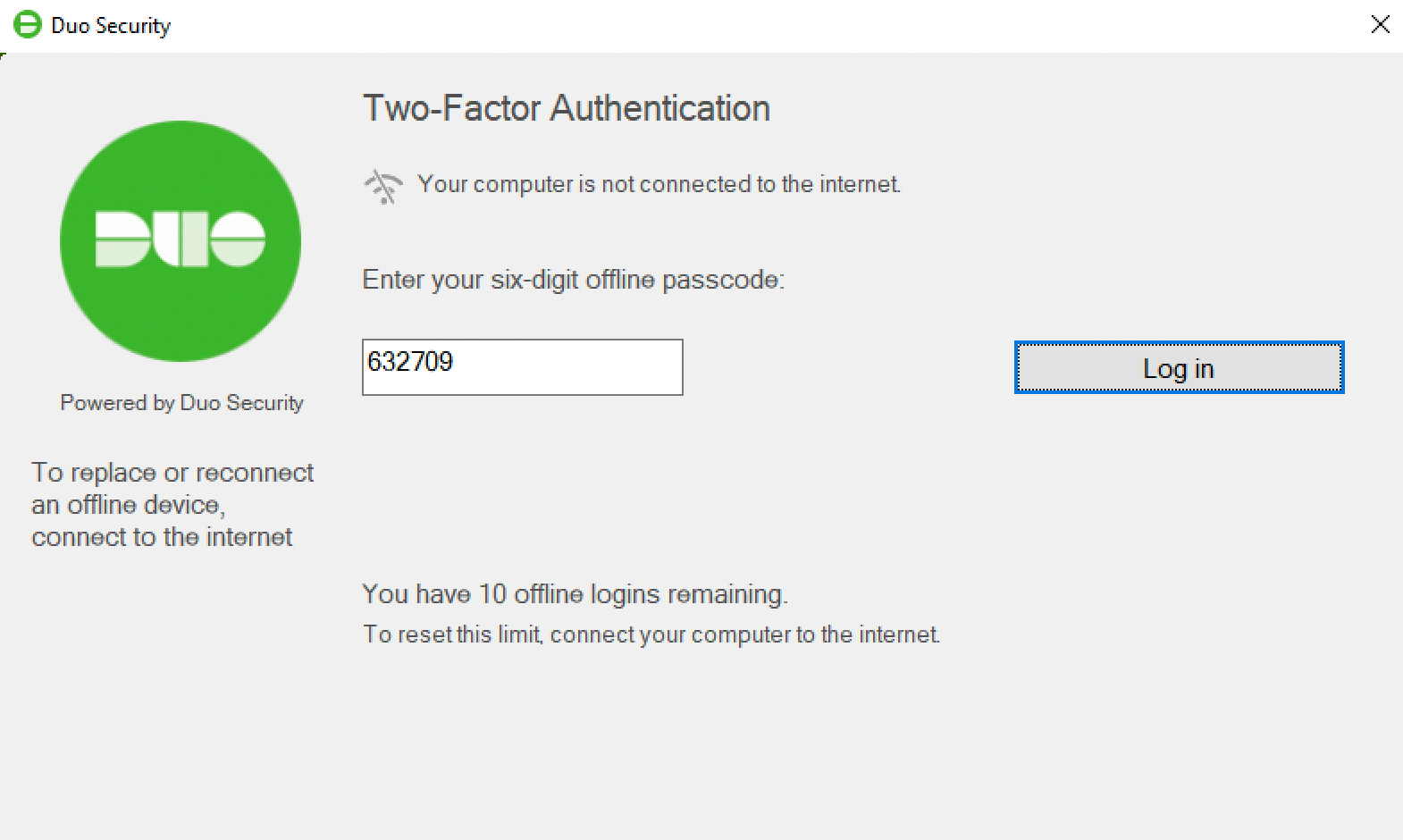
You can besides reactivate offline access from the online Duo prompt. Note that only one authentication device — a single phone with Duo Changeable or a single security system key — may be activated for offline login. Activating a second device via the reactivation process deactivates the maiden.
See the full offline activation and login experience in the Duo User Guide for Windows Logon.
Updating Duo Authentication for Windows Logon
You can upgrade your Duo installation over the present interpretation; there's no need to uninstall first. The installer maintains your existing application information and configuration options.
-
Download the most recent Couple Authentication for Windows Logon installer package. View checksums for Duo downloads here.
-
Fly the coop the installer with administrator privileges and follow the on-screen prompts to complete the upgrade instalmen.
If you're upgrading to a adaptation that includes new installer options, the conformation screen for those options won't atomic number 4 shown during an upgrade set up. You'll need to configure those new options via Regedit or GPO update. See the Configuration section of the FAQ to learn how to enable and configure Duo for Windows Logon options in the registry, or the Group Insurance certification to pick up how to configure options with GPO.
Uninstalling Duad
If you'd like to remove Duo Authentication for Windows Logon from your system, open the Windows Curb Panel "Programs and Features" applet, suction stop on the "Duo Authentication for Windows Logon" program in the list, and then click Uninstall.
High Deployment and Shape using Chemical group Policy
Delight reckon our Duo Authentication for Windows Logon Group Policy documentation.
Troubleshooting
Need some help? Have a look at the Windows Logon Frequently Asked Questions (FAQ) page or try searching our Windows Logon Knowledge domain articles or Biotic community discussions. For further assistance, touch Support.
If the Duo application program denies memory access to your users, ensure that you have enrolled them in Distich with a username or username false name that matches the username they use to log into Windows, and with a 2FA device attached that is excited for Duo Push, can receive ring calls from Duo, or can generate a one-time passcode. If you applied a new user policy that allows access without 2FA and expect it to set aside the blocked users through that the blocked users do not exist in Duo. Pertain to these articles to learn more about user enrollment states and how they merge with policy settings to bear upon user logins.
- Why are Duo users being prompted to enroll Beaver State denied access when my New User Policy is readiness to allow access without 2FA?
- Guide to Duo User Enrollment States
Network Diagram
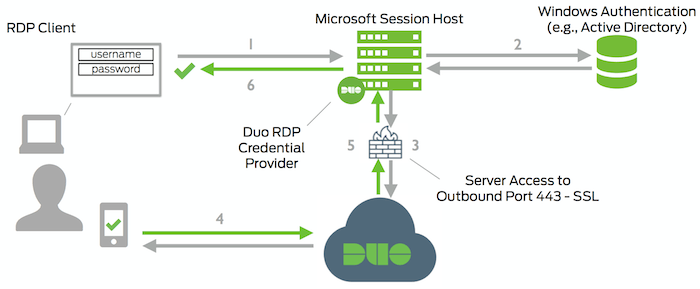
- RDP connection, console logon, or UAC elevation initiated
- Capital authentication of Windows credentials (domain Oregon local substance abuser)
- Duo Windows Logon credential provider joining established to Duo Security complete TCP port 443
- Secondary authentication via Duo Security measures's armed service
- Duo Windows Logon certificate provider receives authentication response
- RDP or console session logged in
two factor authentication windows 10 login
Source: https://duo.com/docs/rdp